Hi there! This post will explain what I had to do to get strongSwan establishing a VPN connection to my FRITZ!Box.
I have the following setup:
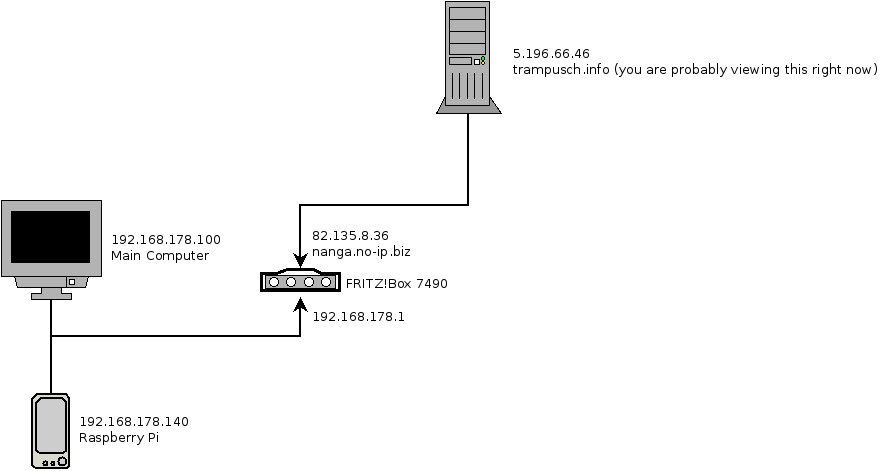
I wanted the server “trampusch.info” to tunnel in my local network, so that it is reachable under a local IPv4 address, e.g. 192.168.178.202. I have some use cases that only work with targets in my local network, e.g. file transfer via SMB.
After some research I decided to use strongSwan as the client software.
Enabling incoming VPN connections in the FRITZ!Box
To allow incoming VPN connections you have to add a new user. I had to go to System -> FRITZ!Box Users -> add user. Select a username and a password. I did uncheck every setting, except for VPN connections of course. After saving you will see a dialog, containing the VPN connection credentials.
Configure the server to connect with strongSwan
This is the config I use. Although it did not work at first, the config itself is correct.
# /etc/strongswan/ipsec.conf, /usr/local/etc/ipsec.secrets (the latter one is in my case correct)
# the explanation of this parameters can be found at:
# https://wiki.strongswan.org/projects/strongswan/wiki/ConnSection
config setup
uniqueids=no
#charondebug="ike 4, knl 4, cfg 4, mgr 4, chd 4, dmn 4, esp 4, lib 4, tnc 4"
conn %default
# unfortunately the FRITZ!Box does not seem to support stronger encryption
ike=aes256-sha-modp1024!
esp=aes256-sha1
ikelifetime=60m
keylife=20m
rekeymargin=3m
keyingtries=1
# the FRITZ!Box support ikev1 only.
keyexchange=ikev1
conn wb
auto=add
# the user identity
xauth_identity=USER_NAME_HERE
left=5.196.66.46
leftid=keyid:USER_NAME_HERE
leftsourceip=%config4
leftauth=psk
leftauth2=xauth
right=nanga.no-ip.biz
rightid=%any
rightsubnet=192.168.178.0/24
rightauth=pskHowever, at first it did not work:
The problem regarding the INVALID_INFORMATION was pointed out on ServerFault.
You get this error if you configure the subnets incorrectly.
With 0.0.0.0/0 as leftsubnet you would be able to connect.
leftsubnet=0.0.0.0/0 would have the consequence, that all traffic of my server would be routed through my home router - that I want to avoid this is obvious ;-).
The core of the problem is that the CentOS RPM package of strongSwan does not contain the unity-plugin, which allows to narrow down the target traffic selectors.
To check if you have installed the unity plugin, you can search for libstrongswan-unity.so on your machine.
If it does not exist, you probably do not have the plugin.
I did not have the unity plugin and therefore had to recompile strongSwan. You should uninstall strongSwan prior compiling it. To compile it with unity, you can do something like:
Compiling strongSwan with the unity plugin enabled
wget https://download.strongswan.org/strongswan.tar.gz
tar -xzvf strongswan.tar.gz
cd strongswan-5.3.5
./configure --enable-unity
make
sudo make installAfter that, place the configs mentioned above in the correct directory (in my case /usr/local/etc), and you are ready to go:
ipsec rereadall
ipsec reload
ipsec up <connection name here, in my case wb>Questions? Suggestions? Comments? I would love to hear from you!